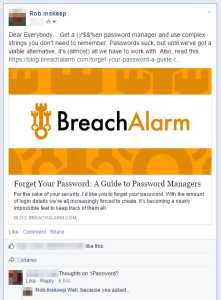
TLDR; No. I don’t especially like the look of it. You have to trust a company who is making money out of (hoping) their product is secure. I personally like KeePass ( http://keepass.info ) which works on all my devices and, coupled with a internet sync service (that also leaves you comfortable with the level of security offered), works on all my devices.
Rob Rant™ …begin!
Any password system (in my opinion) which is not exposed to the rigours of open (source) scrutiny is a little like asking someone’s older brother to hold on to your bag of lollies while you have your turn to bat. You might come back and find them untouched by the other kids that he was able to fend off, but there again, he might just have easily helped himself to them.
It comes down to your level of trust in who you leave your sweet things with (mmm… delicious credentials).
Perhaps a more secure approach would be to convince everyone at the ballpark that they should ALL keep an eye on the lollies to stop anyone helping themselves, and if they wanted their stuff protected, then they could do the same thing.
This communal vigilance makes the items being protected, on the whole, safer. The big kid may be able to physically intimidate others away, but unless he is as vigilant in watching the bag as say, the kid with asthma who is just sitting and watching the others play, then there is still a risk vector waiting to be exploited…
In the big wide world of the Internet, we know that security services and complicit standards agencies have released weakened cryptography ciphers, we know that spy chiefs are continuing to call for back doors to cryptography found in consumer-level devices, we also know that certain countries can, and are, forcing companies within their control to allow them to surveil their customer base (data / traffic) in the name of national security. They are also making it an offence for these companies to tell anybody that this is occurring (Ref: National Security Letter expansion under the Patriot Act (See Part VII of this article)
“Under the Patriot Act provisions, law enforcement can use NSLs when investigating U.S. citizens, even when law enforcement does not think the individual under investigation has committed a crime. The Department of Homeland Security has used NSLs frequently since its inception. By using an NSL, an agency has no responsibility to first obtain a warrant or court order before conducting its search of records.” – Cornell University Law School, Fourth Amendment – An Overview
Ask Joseph Nacchio what happened when he refused to assist with the surveillance of his customers unless the requester was able to get permission to do so via the Foreign Intelligence Surveillance Court. This kind of behaviour makes folks so distrustful of companies within these jurisdictions, that the companies now face a competitive disadvantage when compared to countries who do not have such (widely advertised/proven) policies.
The only solution seems to be to make everyone either complicit, or cohesive in their scrutiny of cryptographic technology. And for everyone to use it. In the same way that the public release of TOR and the ensuing ‘user friendlification’ (<– I just made that term up, you can use it if you buy me beer and don’t lynch me) made it much more easiy to use and accessible to non-technical consumers (and arguably an influencing factor in the 2011 Arab Spring uprising), these consumer level enhancements result in more awareness, more traffic, more processing power and ultimately will ‘break the internet’ (thanks for the sound bite Eric).
Now. It’s important that you, my dear gentle innocent (?!) reader(s) understand that while I was delving into the lens of knowledge (served to me by a company interested in selling information on my browsing habits, interests, interactions and associations (that’d be you lot)…), there should have been a corresponding increase in my ‘might be interesting’ level. I will have been raised up a notch or two on the lists of the various governments who subscribe to such metadata feeds, but where in the list of ‘might be interesting’ this places me is a matter that only the agencies tasked with collecting and tracking threat intelligence will know.
I say should, because looking into this stuff is done for one of two reasons. You are interested in the research (or ‘truth’ if you believe in such a concept), or you are wanting to inform yourself on how to hide something.
Now this thing you want to hide may simply be the credentials you wish to protect from people who shouldn’t know them, or it may be something more nefarious. Either way, by you having an association with me, your ‘might be interesting’ level should also have jumped a notch or two, depending on how many of the above links you follow, or how fast you unfriend me 😉 – Sorry about that!**
*Who should know better than to poke the bear with her ever-so-pointy rant stick
**Not actually sorry about that in the slightest***
***Okay, maybe a little, but not much. It’s good that people are aware of this stuff. It’s unrealistic to demand that they understand how it all works.
In another interaction from the same article posting, a friend called upon her circle of influence to suck it up and start using a password manager. Great result!
But a word of warning on password managers relying on other system components. Personally I’m not a fan of browser based password managers, it’s a bug-chaining thing. If the browser is screwy (not that browsers have ever been a source of ridiculous amounts of vulnerabilities), then then services that rely on it ‘working correctly’ are also on shaky ground.
Now, while I may have unfairly picked on LastPass in my response, it has suffered from its share of vulnerabilities (2011, 2013, 2014) – but it’s not alone.
“Our attacks are severe: in four out of the five password managers we studied, an attacker can learn a user’s credentials for arbitrary websites,”
I partially agree with the retort to my response, yes a password manger is better than no password manager, but only kind of. The problem (with people being oblivious to the flaws that their password manager of choice may have), is that they still believe they are protected, and perhaps place heavier reliance in the tool than they should.
The bottom line is you should only use a password manager you can trust, just like you should get a car whose floor mats you can trust not to get tangled in the (also poorly designed) gas pedal, or window switches that don’t catch on fire. And you should do your due diligence during the selection process of things which are designed to provide an element of safety.
Even today there are iIdiots who are adamant that their beloved brand is impervious to computer malware. You can’t blame the users (too much), when the company they so adore refused to allow their support reps assist users with known malware.